

Elastic Security: Securing your cloud assets with cloud security posture management
Overview
Introduction to Elastic Security
Elastic Security is a unified security solution that brings together SIEM, endpoint, and cloud security into a single platform. This makes it easier to protect, investigate, and respond to security events from all parts of your environment.
In this guide below, you'll learn how to get started with Elastic Security for Cloud Security so you can monitor, detect, and investigate anomalous activity within cloud environments.
Let's get started
Create an Elastic Cloud project
Get started with a 14-day trial. Once you go to cloud.elastic.co and create an account. Be sure to select Security with Elasticsearch then SIEM and Security Analytics. In addition, you should select if you're migrating data from somewhere (for the purpose of this guide we'll select “no”), your preferred cloud regions then when you create your first project.Get started with a 14-day trial. Create an account on cloud.elastic.co and then follow this video to deploy Elastic.
If you click on Edit settings you can choose a cloud provider, including Google Cloud, Microsoft Azure, or AWS.
Once you launch your deployment you'll be brought to the onboarding page. Select Add data with integrations and you'll see a navigation bar after it expands.
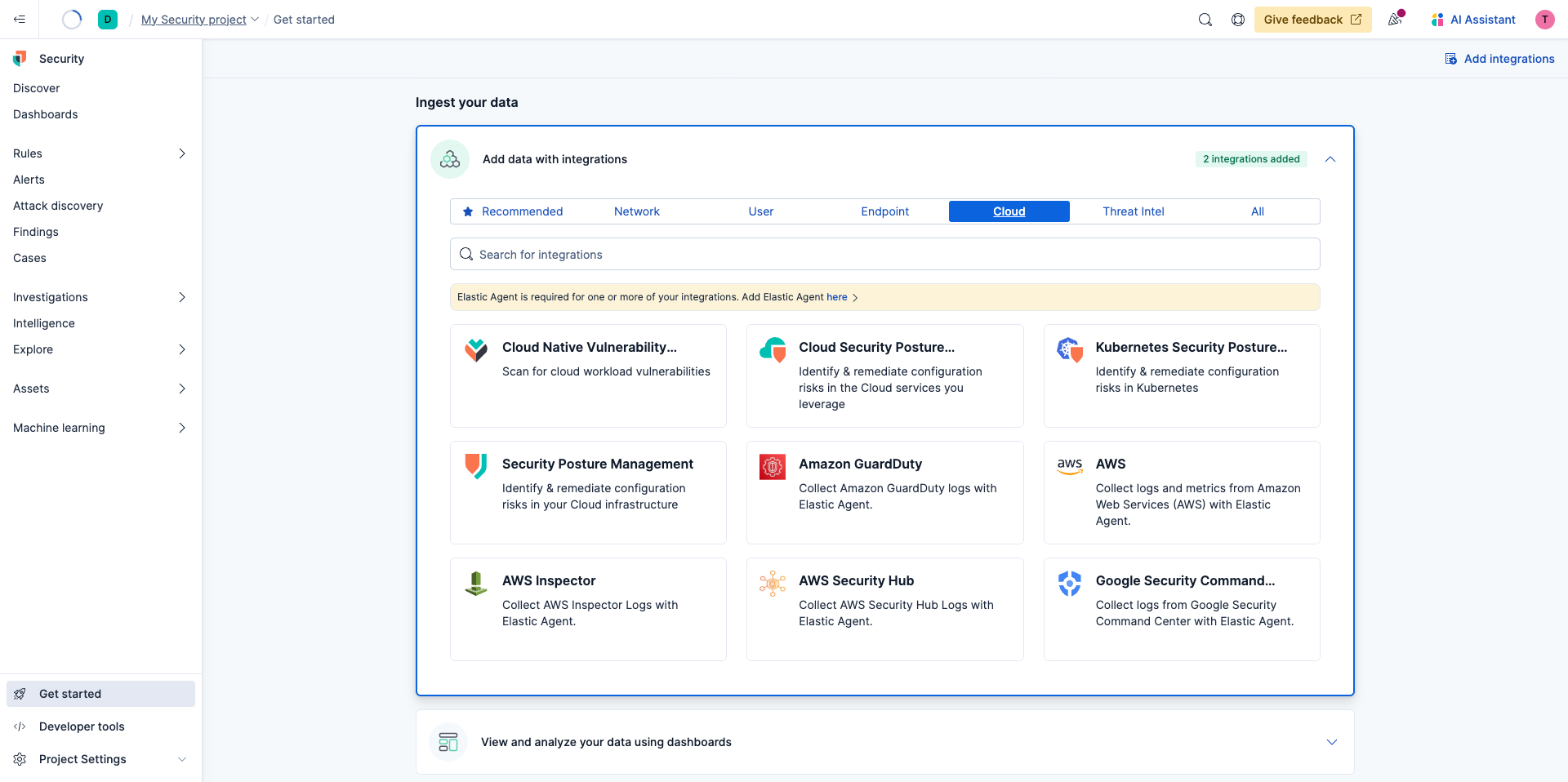
Select Cloud then click Cloud Security Posture Management (CSPM).
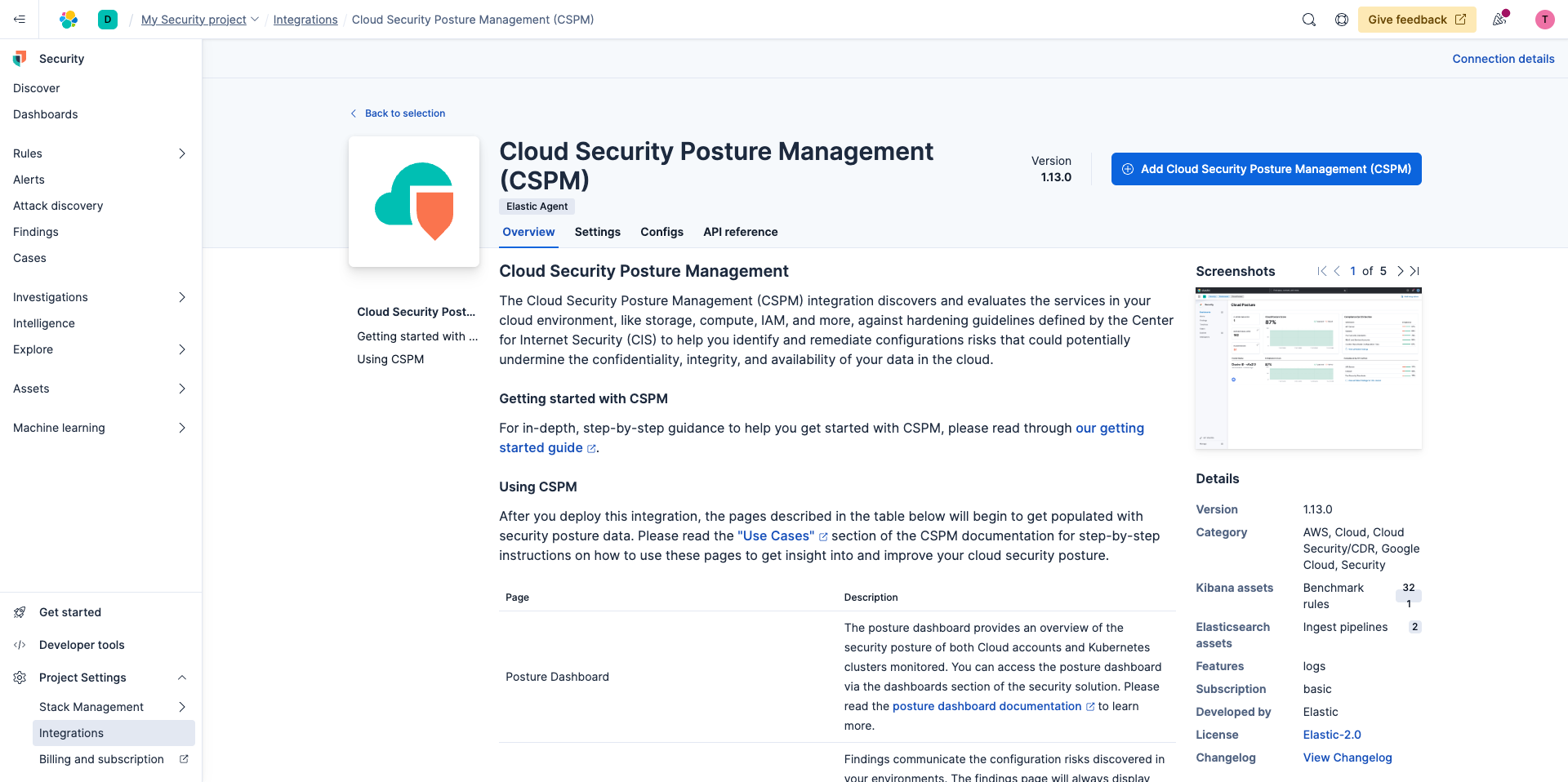
Once you click the Add Cloud Security Posture Management (CSPM) button in the upper right you'll be brought to a page where you'll be prompted to add the integration.
This integration enables discovery and evaluation of services in your cloud environment such as storage, compute, IAM, and more so you can identify and remediate configuration risks that could undermine the confidentiality, integrity, and availability of your data in the cloud.
Next, you'll configure the integration. First, you'll select the cloud provider you want to monitor:
- Amazon Web Services (AWS)
- Google Cloud (GCP)
- Microsoft Azure (Azure)
The Elastic Security for Cloud CSPM feature can be configured to perform evaluations at the organization level to ensure full coverage or at the individual account level within an organization. Note you will need appropriate permissions, scoped for organizational or account-level access, to complete the setup of CSPM. For an initial proof of concept and the purpose of getting started, you'll choose Single Account.
After you give it a name and description, you select your deployment options. For the purpose of this guide, let's choose Agentless for simplicity, for which you only have to provide credentials for your cloud account.
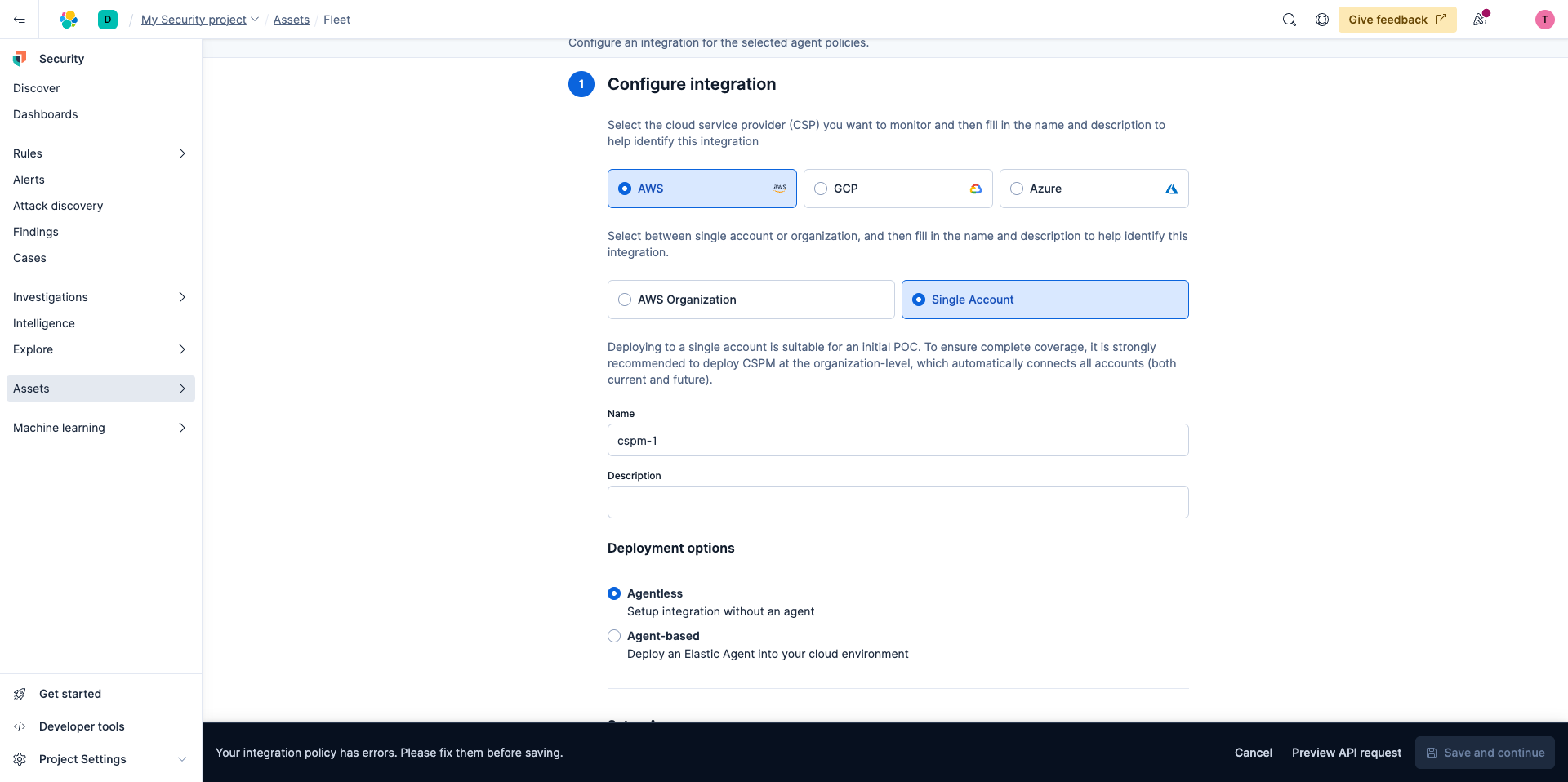
Once you select Agentless you'll be asked how you want to set up access. Let's stick with Direct access keys. You'll notice when you select Direct Access Keys you'll see instructions below when you can expand.
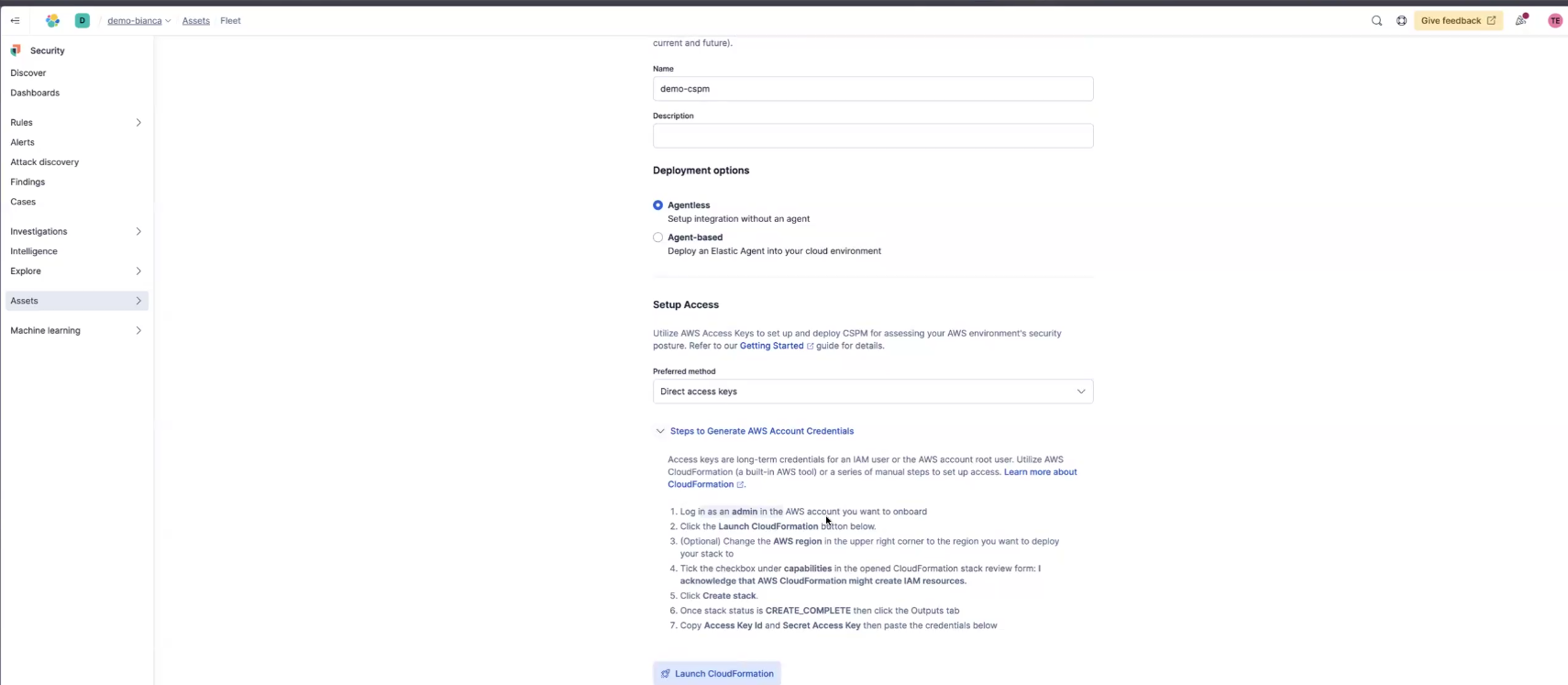
So next select Launch CloudFormation Which will create the credentials with the right scope permissions for you automatically.
Now a new tab will open and you'll see a CloudFormation page and you'll need to give the Stack a name, in the Capabilities selection at the bottom select the check box to acknowledge, then click Create stack.
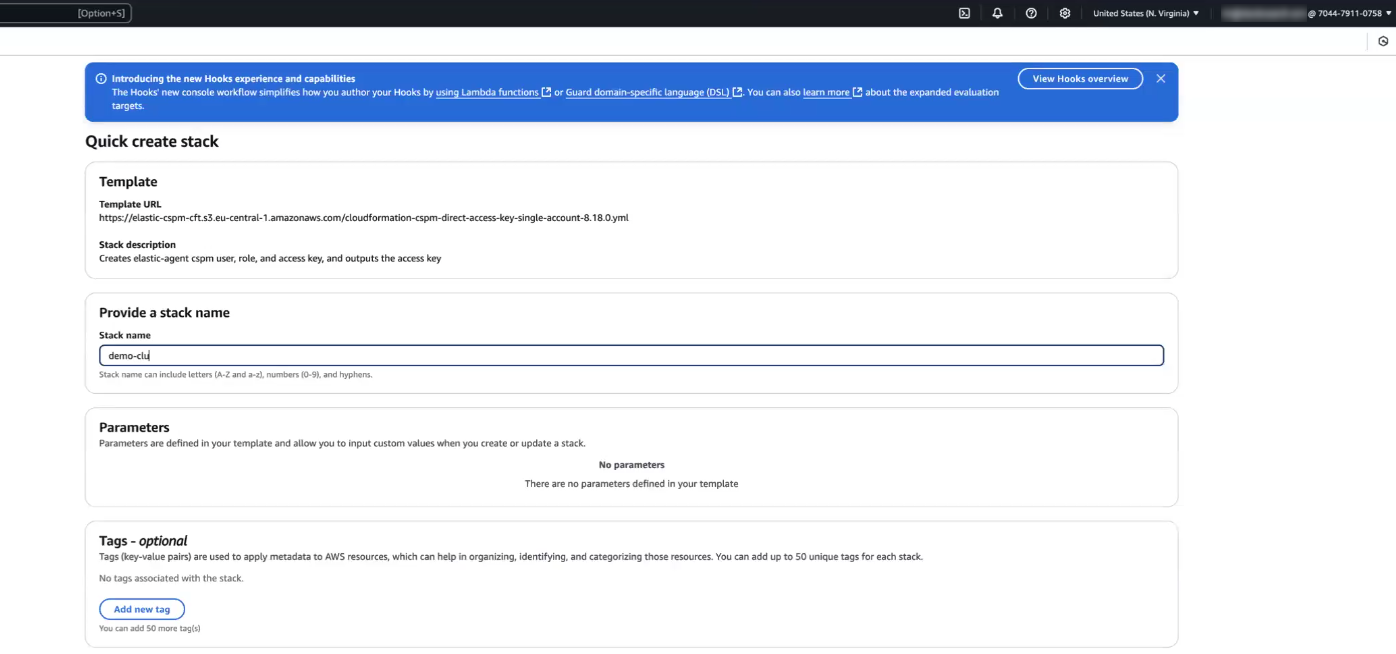
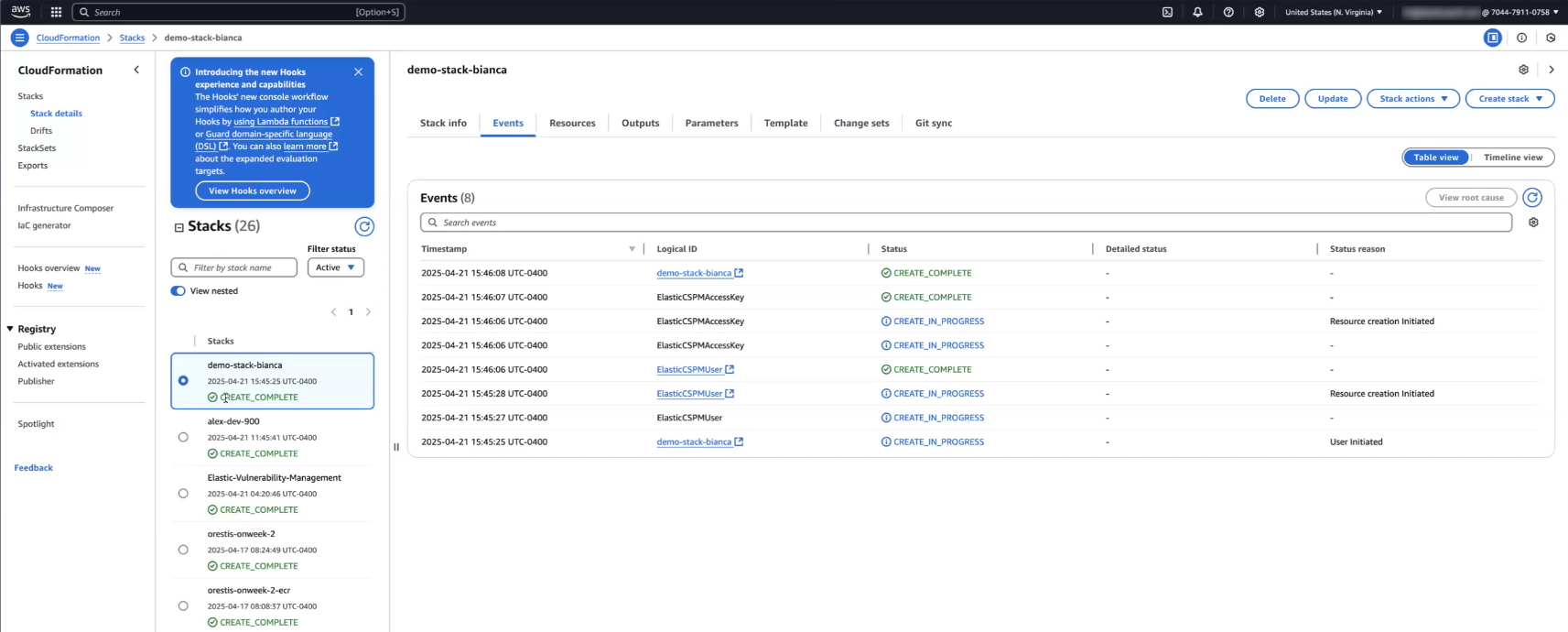
The next page will take a few minutes to finish running and when it does, in the left panel where your Stacks are located you'll see the one you just created and it will say CREATE_COMPLETE.
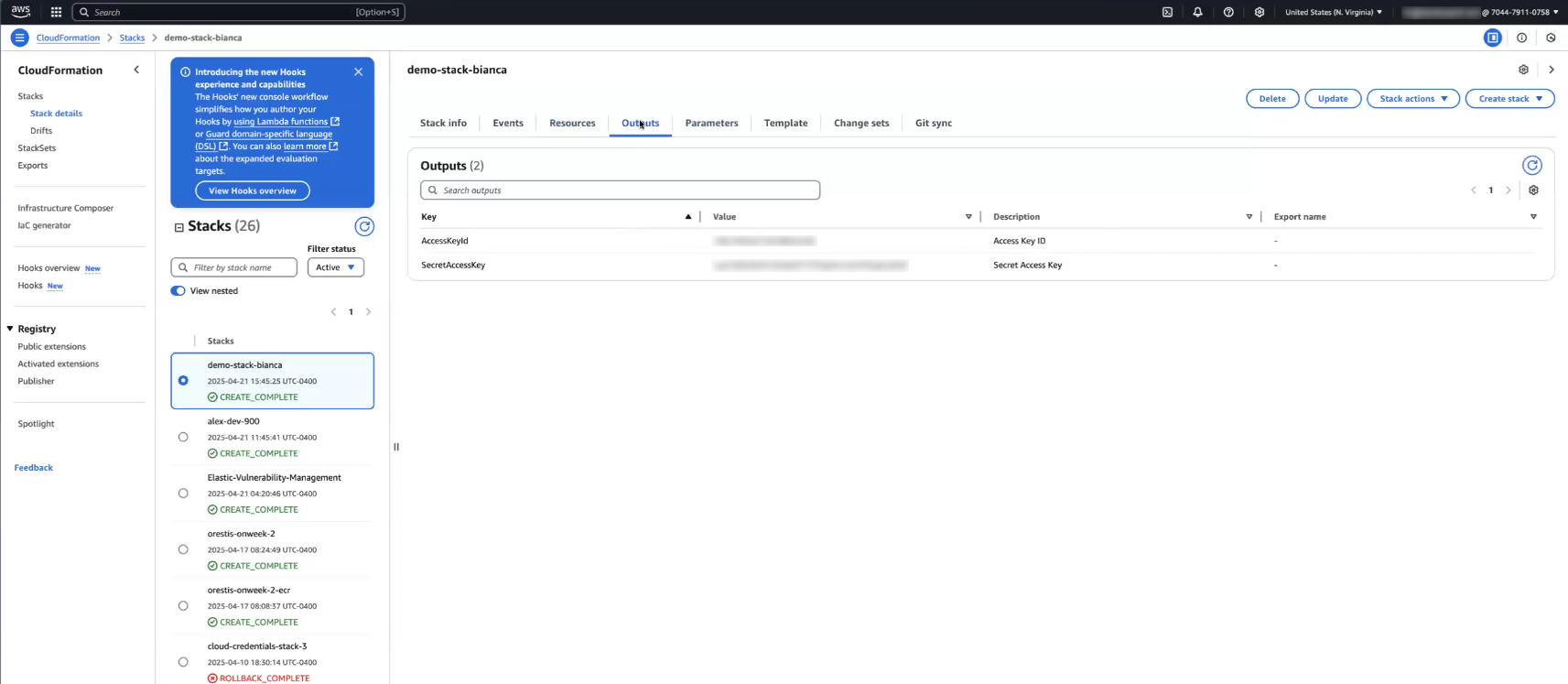
Now at the top select the Outputs tab and you'll see your AccessKeyID and SecretAccessKey.
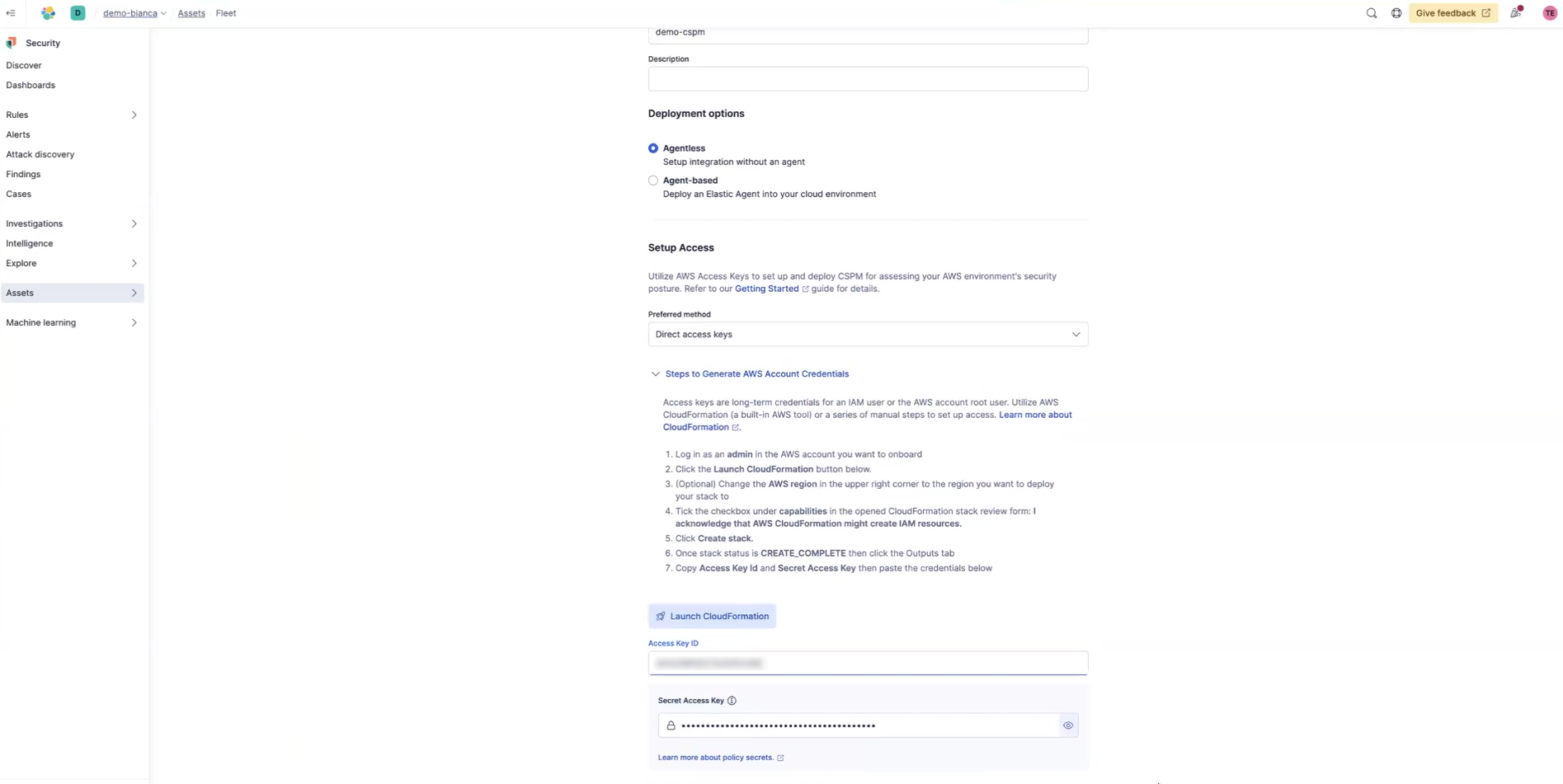
You'll copy both of these over in the Setup Access section then click Save and continue. At this point you'll start seeing data flowing in.
Working with Elastic Security
Prior to getting started with automating troubleshooting ensure you know how to do the following view and analyze your data using dashboards.
Keep in mind that you'll need to do additional configurations if you'd like to enable Cloud Native Vulnerability Management. This isn't needed to get started, but for more information, check out our documentation.
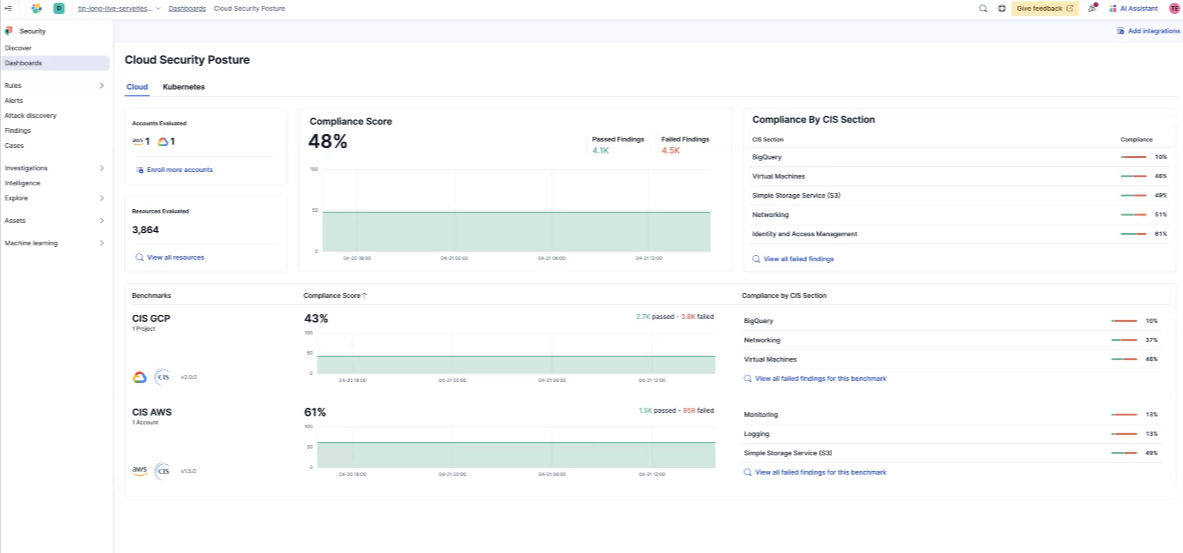
Cloud Posture Dashboard
The Cloud Posture dashboard summarizes the overall security posture of your cloud environments.
- Number of accounts you've enrolled
- Number of resources evaluated
- Failed findings
Your posture score tells you how securely configured your overall cloud environment is.
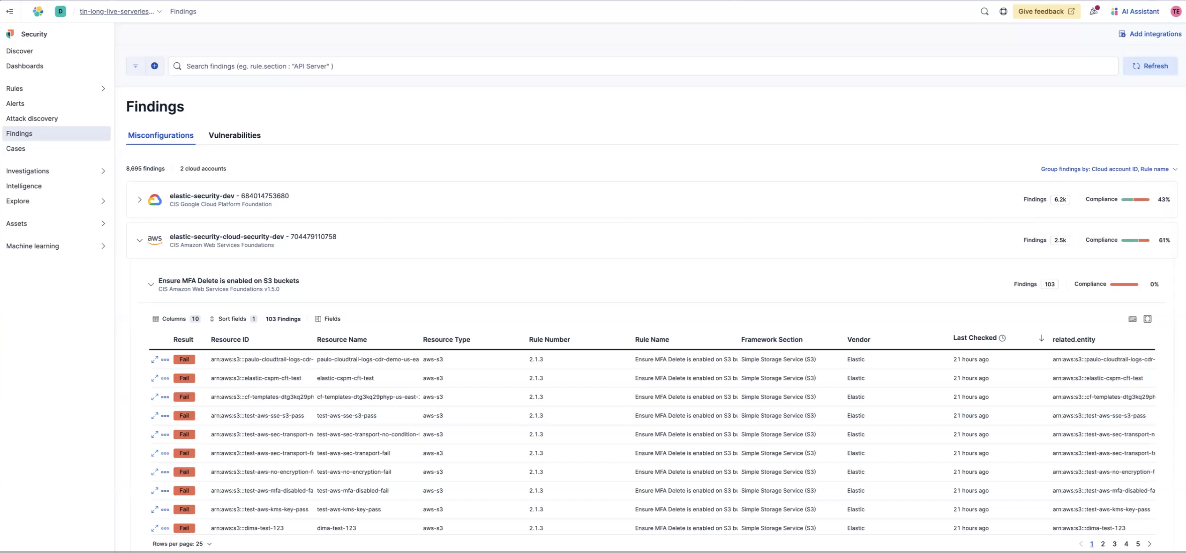
Findings and alerts
The Findings page displays each individual resource evaluated by the CSPM integration and whether the resource passed or failed the secure configuration checks against it, for more information on Findings, such as how to group and filter them, check out our documentation.
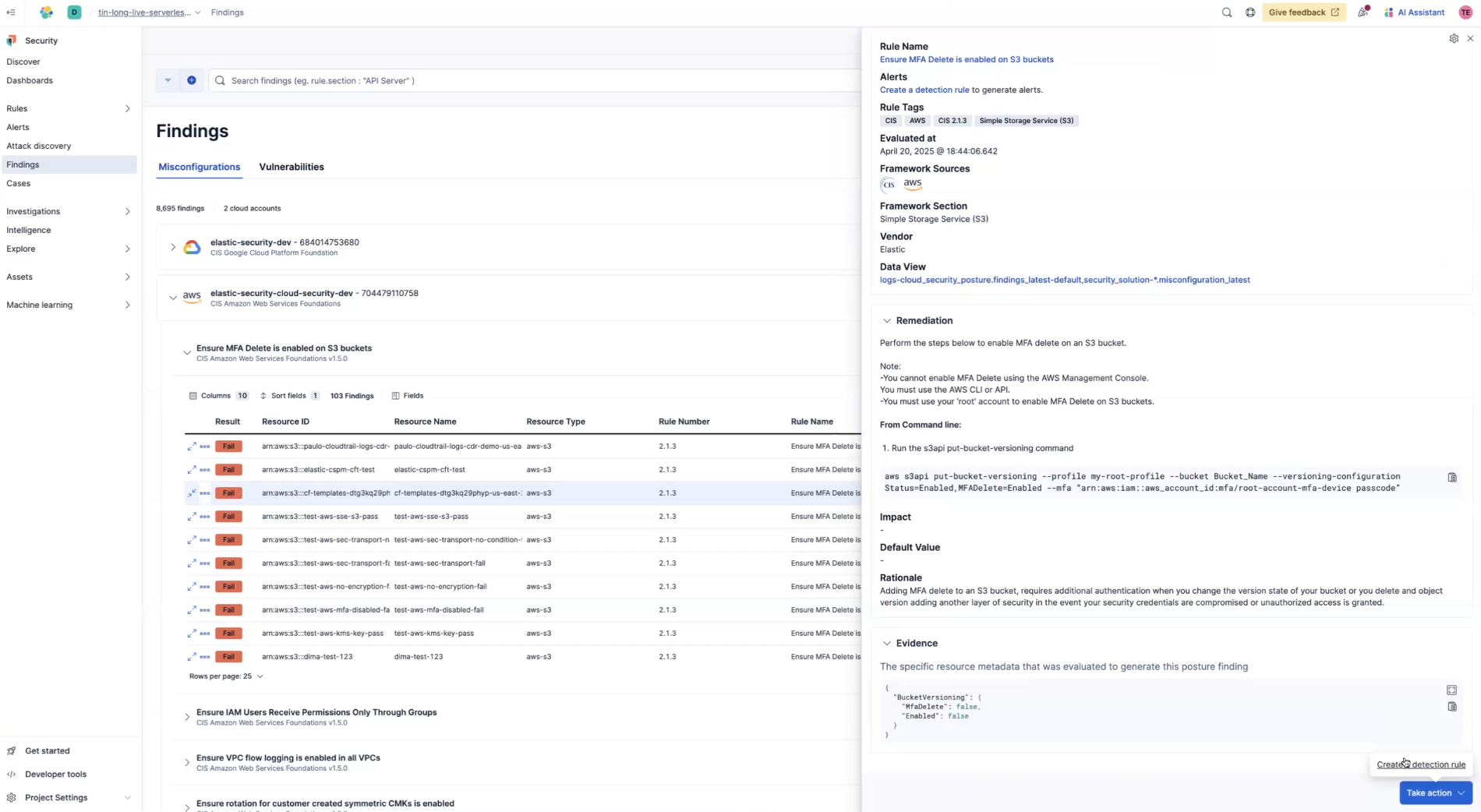
Some rules, more than others, you may want to monitor closely. You can select a finding for that particular rule and click Take action in the lower right. Then click Create a detection rule.
Next click View rule.
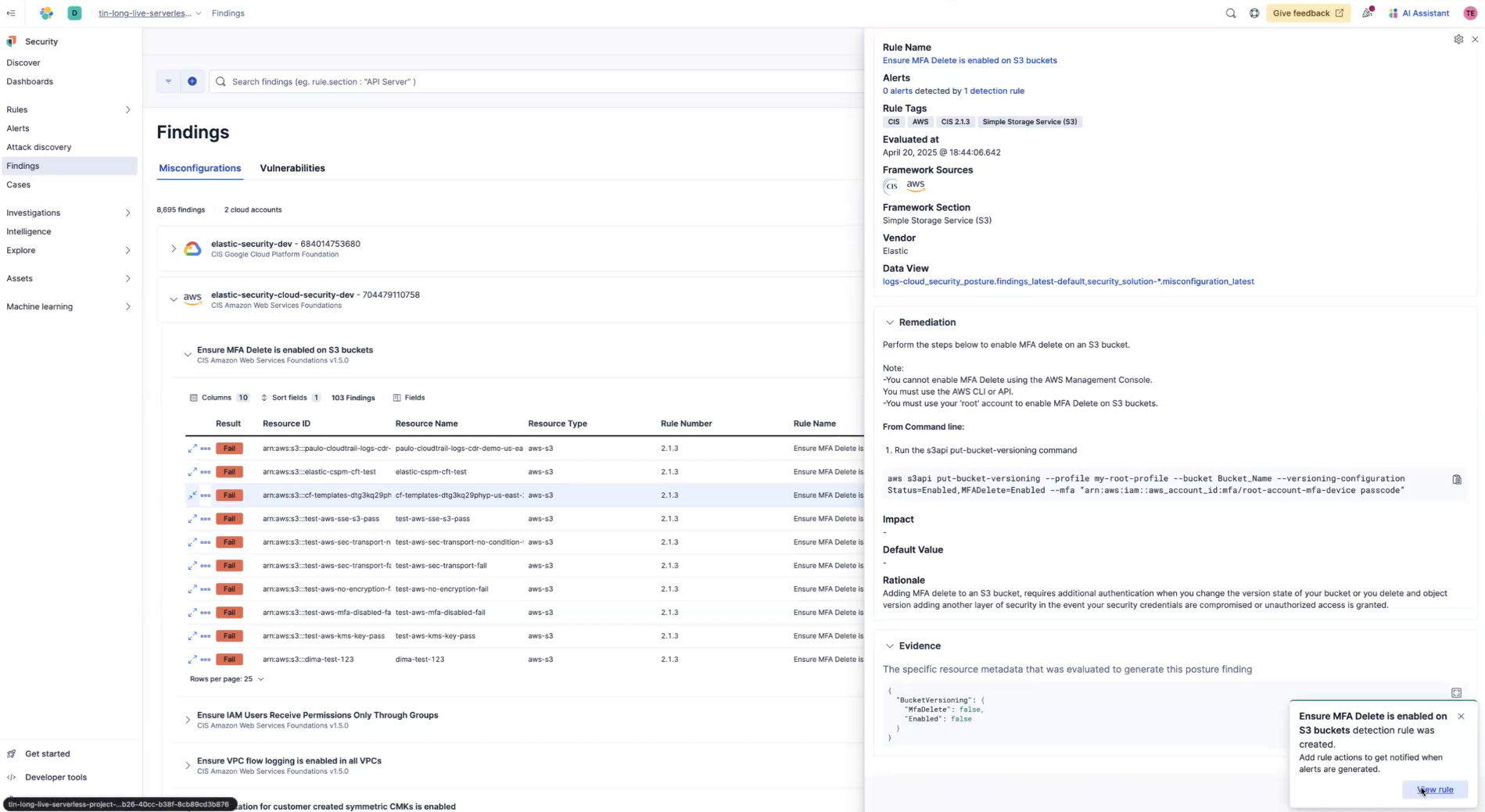
Now, you'll see the detection rule, along with its definition. Now, whenever there is a failed finding for this rule, you'll get an alert. To set up other actions, click Edit rule settings on the upper right of the rule page.
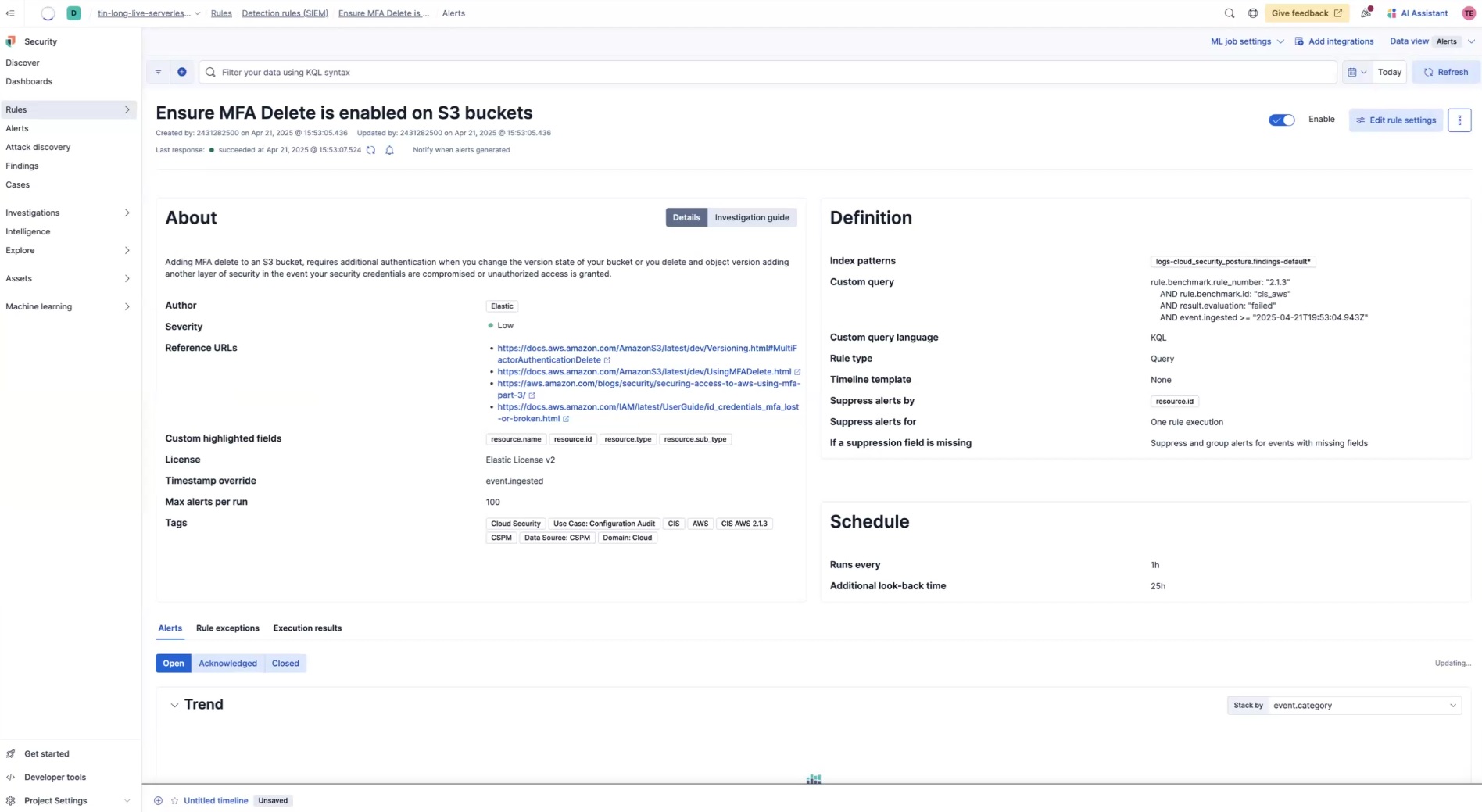
Next you'll select, Actions.
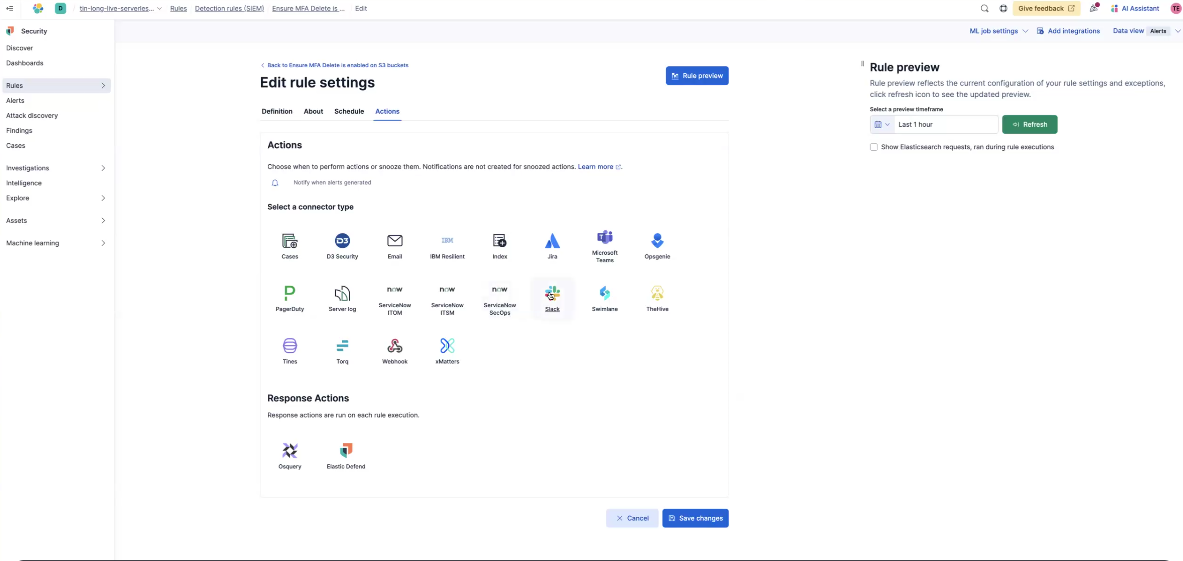
From here, you can set up actions. For example, if a rule fails, you set up a Slack message, Jira ticket, etc., so you get a proactive notification to review the failed finding and remediate the misconfiguration. To learn more about detection rules, check out our documentation.
Next steps
Congrats on beginning your Elastic Security journey with Elastic Security for Cloud (CSPM). For more information on CSPM, please review the product documentation. As you begin your journey with Elastic, be sure to understand some operational, security, and data components you should manage as a user when you deploy across your environment.
Ready to get started? Spin up a free 14-day trial on Elastic Cloud or try out these 15-minute hands-on learnings on Security 101.