From endpoint to XDR: Operationalize Microsoft Defender for Endpoint data in Elastic Security
Enhance your threat detection, investigation, and response by integrating Microsoft Defender for Endpoint data with Elastic Security.
Many security teams often find it difficult to detect and respond to threats because of fragmented visibility and isolated endpoint data. This challenge led to the development of extended detection and response (XDR), which integrates endpoint insights with contextualized data from networks, cloud environments, and identity systems. Endpoint security tools are essential for visibility into endpoint threats, but they only provide a limited view. Endpoint data alone lacks the broader context needed to fully understand and mitigate threats across an organization’s entire attack surface.
True XDR requires a comprehensive approach that goes beyond isolated endpoint telemetry. Elastic Security solves this challenge with AI-driven security analytics, delivering unified threat detection, investigation, and response without the need for yet another XDR tool. Elastic provides a single platform that eliminates silos, reduces tool sprawl, and cuts unnecessary costs — providing a more efficient and holistic defense against modern cyber threats.
Elastic Security integrates with Microsoft Defender for Endpoint (MDE) and operationalizes MDE data alongside signals from network, identity, and cloud sources, offering a complete threat picture. By ingesting MDE telemetry, whether directly or via Microsoft 365 Defender (Microsoft Defender XDR), into Elastic Security, organizations can gain deeper visibility and take decisive security actions with advanced analytics, AI-driven assistance, and robust response capabilities. Backed by Elastic Security Labs’ threat research and machine learning, Elastic’s open security ecosystem ensures that defenders can correlate MDE alerts with other data sources, accelerating investigations and enabling proactive threat mitigation.
Integrating Microsoft Defender for Endpoint with Elastic Security
Microsoft Defender for Endpoint provides deep insights into endpoint threats, but integrating its data into Elastic Security significantly enhances its effectiveness by placing endpoint telemetry within a broader security context as part of the XDR strategy.
Direct MDE integration
Elastic Security offers a dedicated Microsoft Defender for Endpoint integration that allows security teams to ingest MDE alerts and telemetry directly. This enables seamless correlation with other security data, providing an enriched understanding of endpoint threats.
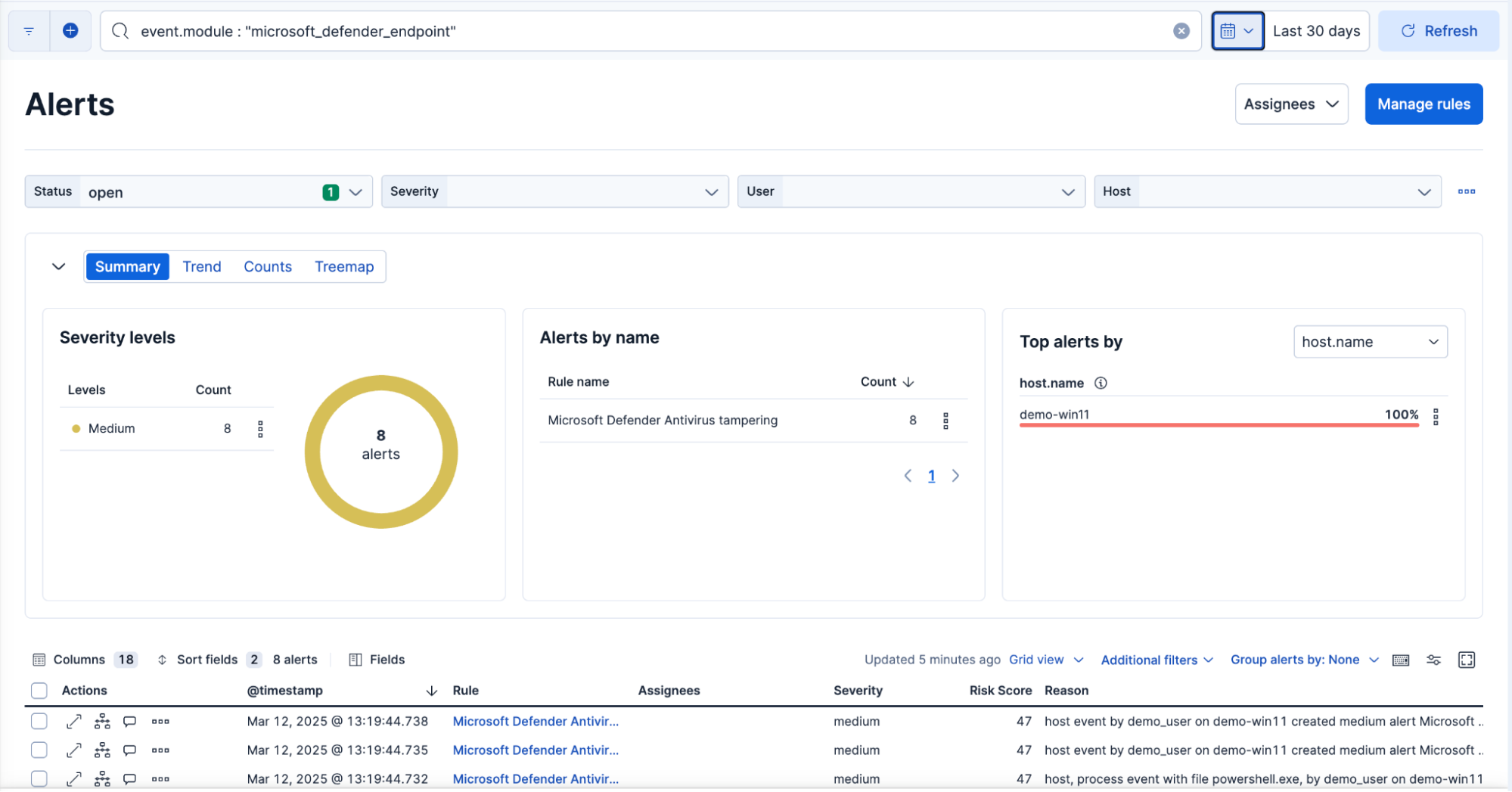
Microsoft 365 Defender integration
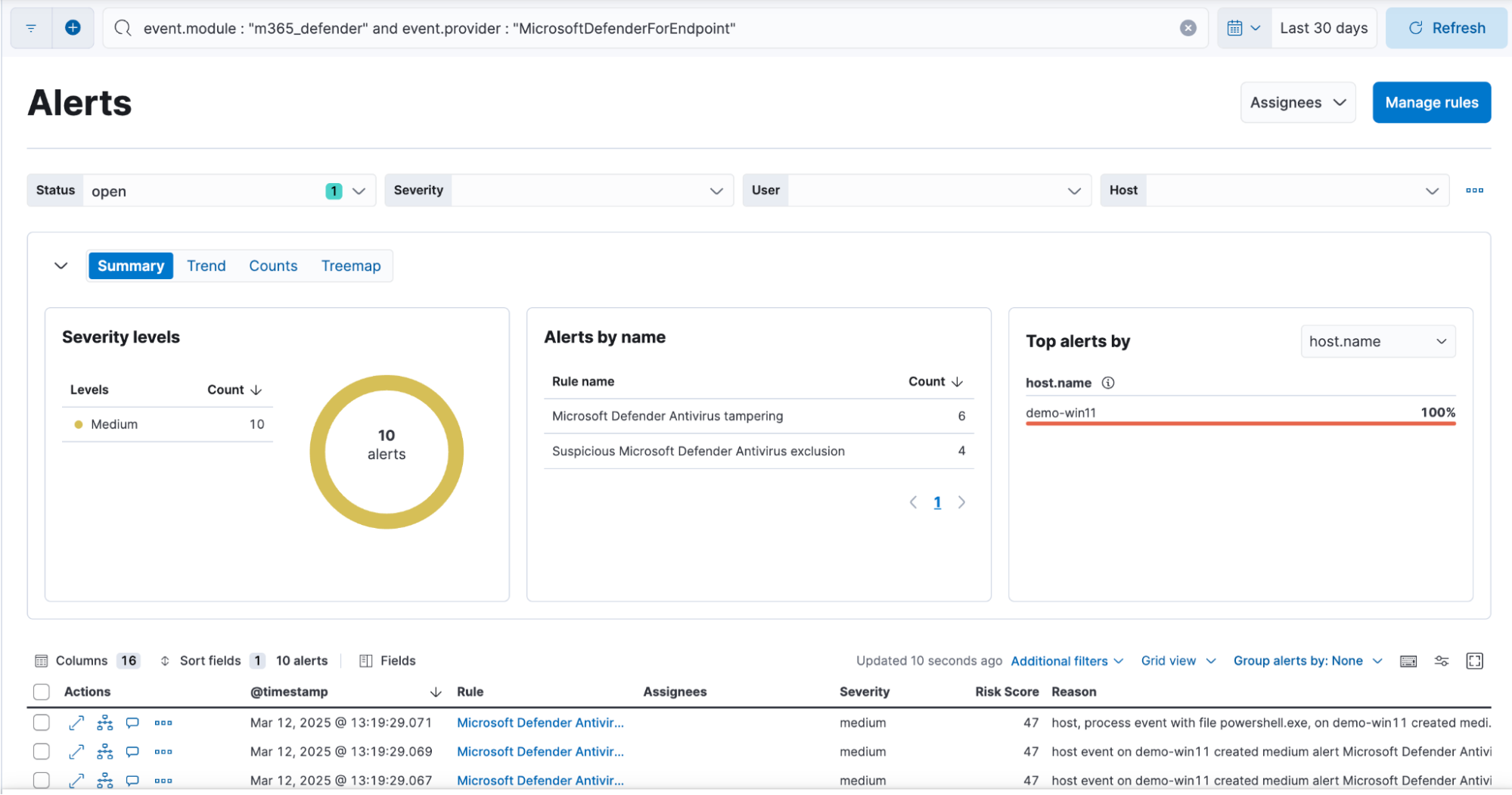
The broader Microsoft 365 Defender (XDR) integration enables ingestion from multiple Defender XDR products, including Microsoft Defender for Endpoint, Microsoft Defender for Office 365, Defender for Identity, and Defender for Cloud Apps, among others. To differentiate MDE-specific data within Elastic Security, teams should use the event.provider ECS field (event.provider:“MicrosoftDefenderForEndpoint”) as another filter on top of m365_defender event.module ECS field. This filtering capability allows analysts to isolate endpoint-related events while still leveraging the full breadth of XDR telemetry.
By unifying MDE telemetry with other security domains, Elastic Security provides centralized visibility, ensuring that endpoint alerts are analyzed within the broader attack surface. SOC teams can instantly correlate MDE alerts with network traffic, cloud activity, and identity-based signals, enabling faster detection of sophisticated threats.
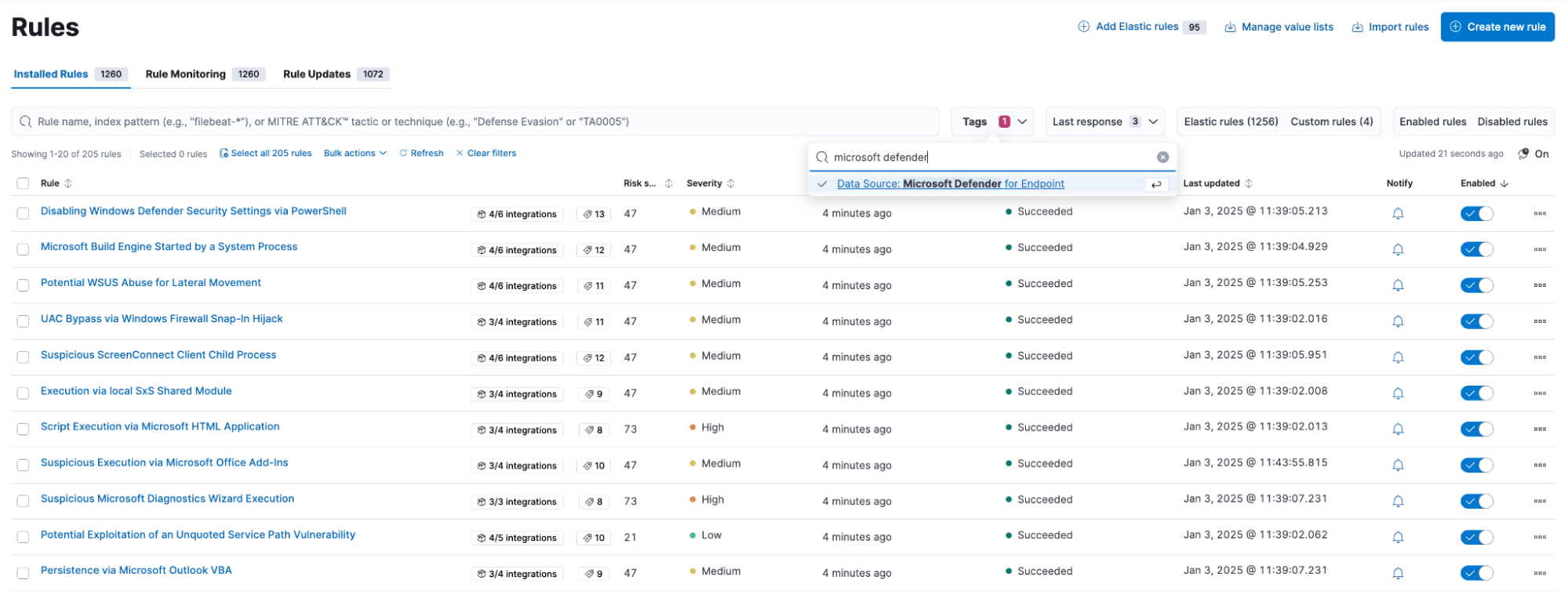
Threat detection with Elastic’s AI-driven security analytics
Elastic Security brings powerful detection and response capabilities to Microsoft Defender for Endpoint data. By ingesting MDE telemetry, security teams can immediately leverage Elastic’s extensive library of prebuilt detection rules, behavioral analytics, and machine learning models — without needing to build custom analytics from scratch.
Elastic’s machine learning models detect anomalies in MDE data, identifying suspicious behaviors that traditional rule-based detections might miss. Analysts can also define custom rules to tailor detections to their organization’s unique threat landscape. Because Elastic’s detection engine operates on an open, extensible data model, organizations benefit from unified detections spanning endpoints, cloud workloads, identity systems, and network data.
Investigate MDE data with Elastic Security
With MDE data centralized in Elastic, security teams benefit from a rich set of investigation tools that enhance threat hunting and response workflows.
Elastic AI Assistant: Accelerating investigations with AI-driven insights
The Elastic AI Assistant for Security brings generative AI into security operations, enabling analysts triaging MDE alerts more efficiently. Security teams can use natural language queries to gain explanations, recommendations, and context around alerts.
Alert explainability and remediation suggestions
Elastic AI Assistant for Security can analyze and summarize MDE alerts to clarify the cause and significance of a security alert. For example, when MDE generates an alert about a suspicious antivirus tampering, an analyst can ask the AI Assistant, "What does this alert indicate and what are the recommended actions?" The assistant will provide a breakdown, detailing why the alert was triggered and potential threat implications. It can also suggest remediation steps, such as isolating the host or searching for related activity across the environment.
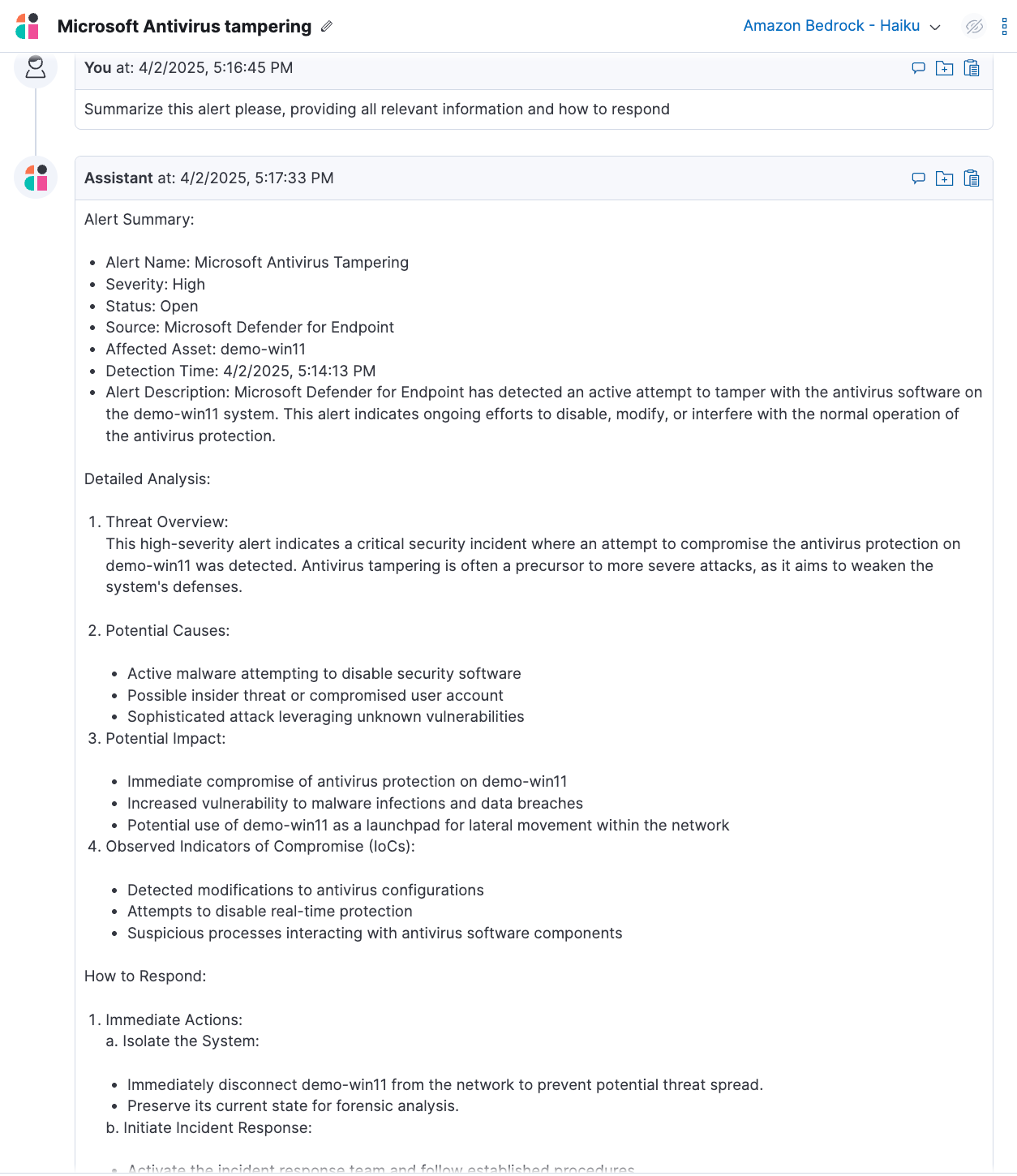
Custom knowledge source integration
Elastic Security 8.16's AI Assistant now integrates with custom knowledge sources, including threat intelligence feeds, internal playbooks, and wikis, to deliver answers tailored to an organization's specific security practices and threat landscape. Analysts can leverage their environment's unique procedures and past incidents when investigating alerts. For example, an analyst could ask, "Have we identified the presence of this malware file in our environment before?" and the AI Assistant would search indexed internal incident reports or threat intel feeds in Elastic for relevant information.
Attack Discovery: Automated threat correlation
Elastic Security’s Attack Discovery automatically correlates MDE alerts with other security events, mapping them to MITRE ATT&CK tactics. This AI-driven correlation helps analysts identify attack chains, reducing manual investigation efforts and enabling quicker responses.
For example, if MDE detects credential dumping on a server, Attack Discovery can link this event to other identity-related anomalies, highlighting a potential lateral movement attempt.
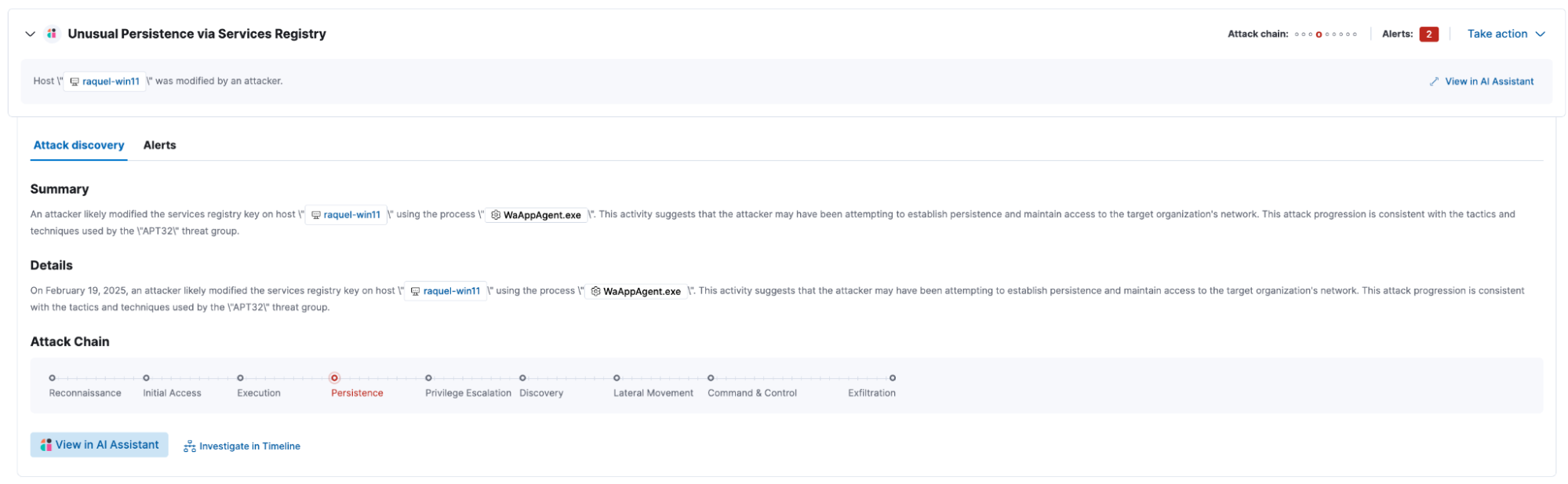
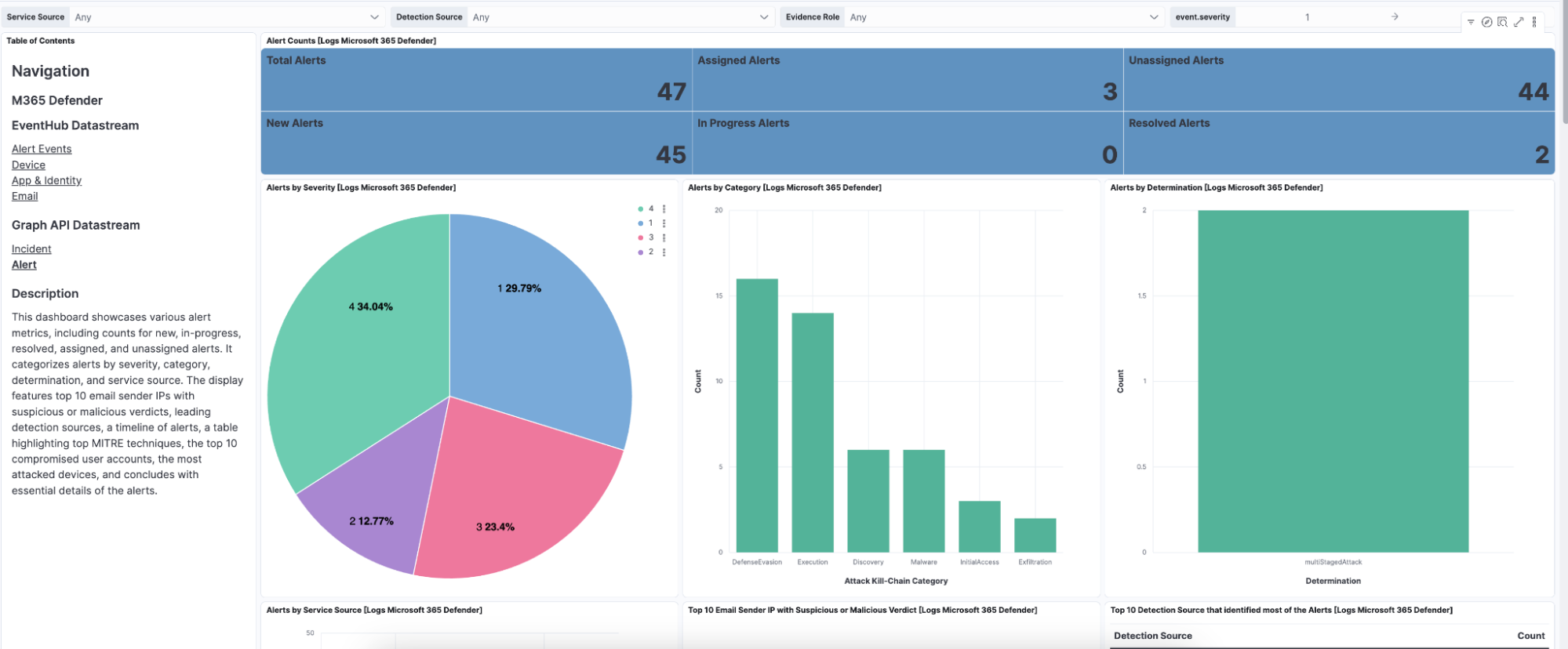
Interactive dashboards and visualizations
MDE data becomes instantly actionable through Kibana dashboards, offering real-time insights into endpoint alerts, attack patterns, and security trends. Analysts can trace process activity using the Analyzer, reconstruct incidents with Timelines, and visualize threat actor behaviors mapped to MITRE ATT&CK.
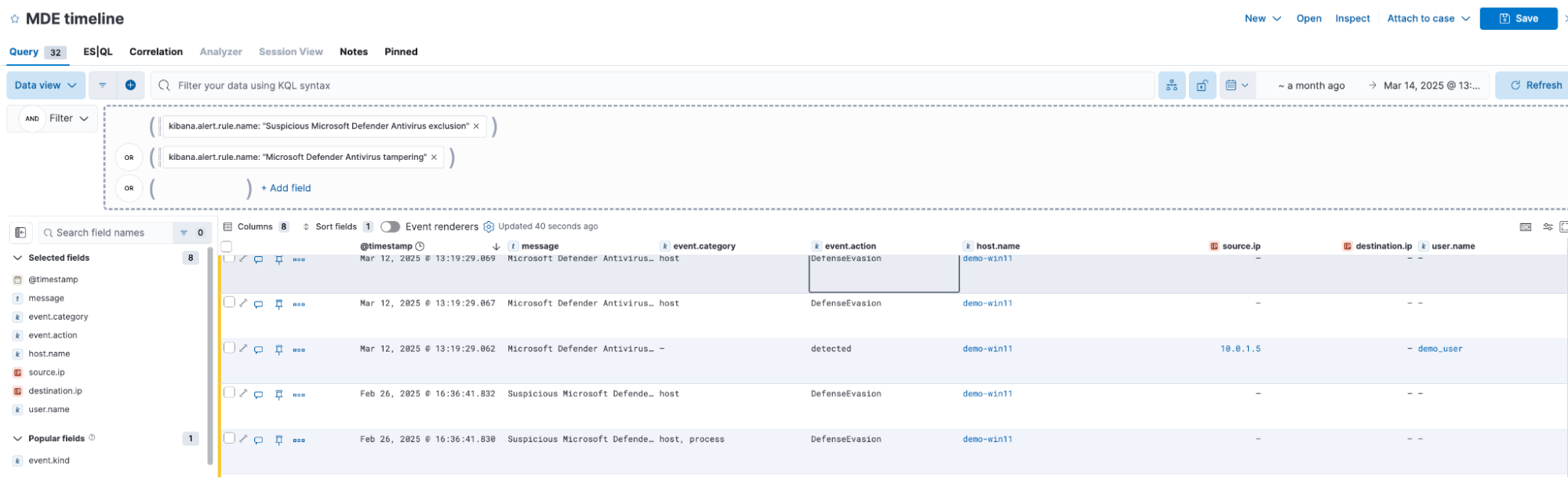
Correlate MDE telemetry with Timelines
Timelines allow analysts to reconstruct security incidents by correlating MDE alerts with other data sources. For example, if MDE detects a malicious executable, analysts can use Timelines to correlate this event with suspicious login activity from the same host, uncovering potential attacker behavior.
Taking action on MDE alerts
Elastic Security now supports bidirectional response actions for MDE, allowing analysts to isolate and release an endpoint in order to contain threats directly from the Elastic interface without switching between tools. By integrating these response actions, security teams can dramatically reduce mean time to respond (MTTR) and limit attacker dwell time.

Long-term visibility and advanced analytics
The more high-fidelity data organizations bring into Elastic Security, the stronger their security posture becomes. While Microsoft Defender for Endpoint provides deep endpoint visibility, it is crucial to consider long-term data retention and analytics capabilities. Elastic Security offers cost-effective long-term data retention, scalable storage options that enable security teams to maintain access to historical data for compliance, forensic investigations, and advanced threat-hunting use cases.
Organizations can use searchable snapshots to retain Microsoft Defender for Endpoint telemetry without the need for frequent rehydration. This allows analysts to perform historical threat-hunting and forensic analysis on years' worth of security data with minimal storage costs. Additionally, Elastic’s cross-cluster search capabilities allow teams to correlate Defender for Endpoint telemetry across multiple Elastic deployments, ensuring a unified security view across different environments.
Beyond storage, Elastic’s Search AI Lake enables advanced analytics and machine learning on Defender for Endpoint data. Security teams can apply behavioral analytics, anomaly detection, and custom machine learning models to uncover sophisticated threats that traditional detection rules may miss. Elastic’s open, extensible ecosystem ensures that Defender for Endpoint telemetry is not just stored, but actively leveraged to strengthen security operations over time.
By centralizing Microsoft Defender for Endpoint data in Elastic Security, organizations gain a robust security data lake that provides deep visibility, powerful analytics, and strategic long-term security insights.
Reducing blindspots with Elastic Defend
In many organizations that have hybrid environments, Microsoft Defender for Endpoint is deployed in some, but not all, endpoints. Elastic Security enables organizations to supplement MDE with Elastic Defend, ensuring comprehensive endpoint protection.
By deploying Elastic Defend on endpoints not covered by MDE, security teams maintain a consistent security posture across their entire environment. All endpoint telemetry — whether from MDE or Elastic Defend — flows into the same Elastic Security workflow, allowing teams to apply uniform detection rules, correlation logic, and automated response actions. This unified approach ensures seamless monitoring and investigation, regardless of endpoint coverage.
Achieving unified, resilient security operations
Integrating Microsoft Defender for Endpoint with Elastic Security delivers a more powerful, unified security operation. This combination enables SOC teams to break down silos, accelerate investigations, and respond to threats with greater confidence. Attackers move across endpoints, networks, and cloud environments, and a platform-based security approach ensures defenders can keep pace.
With Elastic Security, security teams can operationalize Microsoft Defender for Endpoint data, leverage AI-driven analytics, and enhance response capabilities — all within a single, scalable security solution. By unifying endpoint telemetry with broader security signals, Elastic Security enables faster incident response, deeper investigations, and a more resilient security posture.
Get started with Elastic Security
Start your free trial of Elastic Security today and experience the benefits of integrating Microsoft Defender for Endpoint data. Improve your threat response by enhancing your threat detection capabilities and gaining deeper visibility into potential threats before they escalate.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.

